Gpg For Mac
Setting this in data/gpg/gpg.conf will set it globally for all platforms because we need to share the keys. We could specify this with the starter as we do it for the gpg path, but i'd prefer not write into all cfgs before starting the app. The goal of this project is to create a GnuPG front end for Mac OS X. To that extent, it will make installing GnuPG on OS X easier and provide inter application services to access GPG. Also, GPGME wrapper in ObjC will be done.
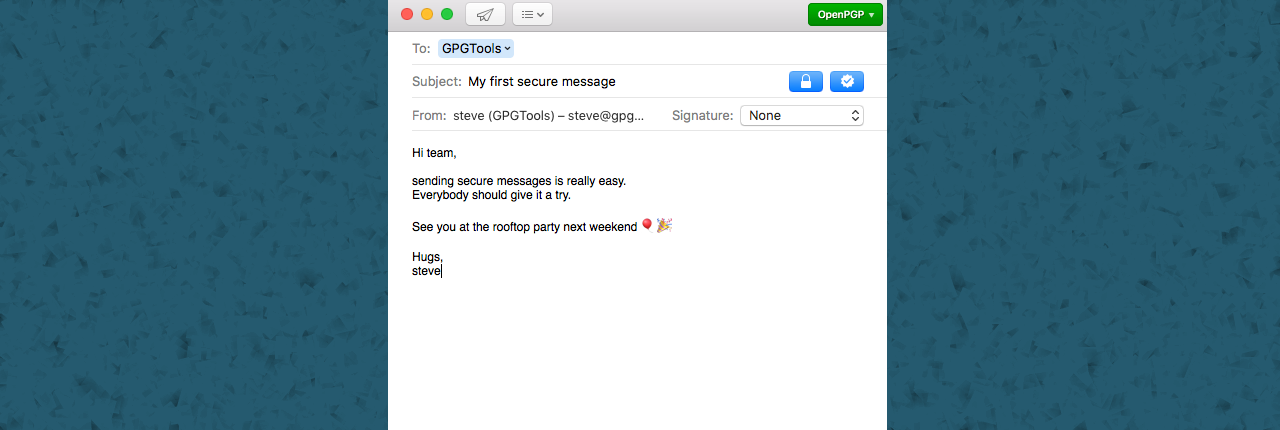
DownloadThe protect and encrypt digital communication for many internet users top priority since it became known that the government on a large scale privacy breach. This is true not only for U.s. security but also for Dutch and European public bodies. A popular free privacy tool for Mac users, GPG Suite.
I looked into dozens of ways to set up PGP on my Mac. A lot of them suck for a plurality of reasons. Across the board, this is the best way for 95% of use cases. Step 1: Install the GPGTools GPG Suite for OS X. This step is simple. Visit the GPGTools website and download the GPG Suite for OS X. Once downloaded, mount the DMG and run the 'Install'. A project to bring GnuPG to Mac OS X with a nice front end and inter application services. I gladly may announce that a new and more active group has taken over the projects that were published on MacGPG. Kleopatra is a certificate manager and GUI for GnuPG. The software stores your OpenPGP certificates and keys. It is available for Windows and Linux. In association with the KMail email client, you can also take advantages of the cryptographical features for your communication via email.
Select and copy the public key text - Then add to your GPG Keyring Looking forward to hearing from you. Want to find out when there are new videos on this channel?
With GPG Suite Mac OS users to email messages if files are encrypted to store. The big advantage of this suite is that it is aimed at Mac users and that the different applications bundles. It is possible to encrypt e-mails and web site URLs to Word or Excel files. The software is completely open source and the developers are dependent on donations for the funding of this project.
Gpg4win is the best alternative for GPG Suite if you are not a Mac but a Windows computer.
To messages from others to be able to read and the recipient of your message to enable your emails to be read, you must both include an encryption key. This makes the program use of OpenPGP. This technology makes use of asymmetric cryptography where two keys are required. One key to encrypt and a different key to decrypt. The use of GPG Suite will be for new users so gevompliceerd. When you run the operation once you understand you have the best possible privacy protection for digital communications. That means that even for specialized government services is nearly impossible to send messages and documents to be intercepted. OpenPGP is the most popular encryption standard. This method is a further development of the in 1991 by Phil Zimmermann written program PGP (Pretty Good Privacy).
With the GPG Keychain feature allows you to manage these OpenPGP keys and you can create, verify and modify. The keys of friends you have to import from a key server. The encrypt and extract e-mail messages by GPG Suite provided via an open source plugin for Apple Mail.
GPG Suite has the following features:
- a combination of encryption tools,
- makes use of the OpenPGP technology,
- encrypted e-mail sending,
- extra buttons directly in Apple Mail for encryption and signing,
- integration with key server to encryptiecodes to share,
- codes from friends via the integrated role import,
- quickly switch between PGP and S/MIME mails,
- emails 'sign' that you are sure is who the message is sent,
- only suitable for Mac OS operating systems.
GPG Suite screenshots
You can free download GPG Suite and safe install the latest trial or new full version for Windows 10 (x32, 64 bit, 86) from the official site.
Devices: Desktop PC, Laptop (ASUS, HP, DELL, Acer, Lenovo, MSI), Ultrabook
OS: Professional, Enterprise, Education, Home Edition, versions: 1507, 1511, 1607, 1703, 1709, 1803, 1809
Updated10 August 2016
Mozilla Thunderbird is free and open source software that allows you to exchange and store email for multiple accounts with multiple service providers. Enigmail and GnuPG improve the security and privacy of your email correspondence by adding support for OpenPGP end-to-end encryption to Thunderbird. They also allow you to sign your messages digitally and verify the digital signatures of others.
- The ability to manage multiple email accounts using a single tool
- The ability to read and compose messages while disconnected from the Internet
- The ability to send and receive encrypted email
- The ability to digitally sign your emails and authenticate signed email from others
Thunderbird is a free and open source, cross-platform email client for sending, receiving and storing email. An email client is an application that lets you download and manage your messages — from multiple accounts with multiple providers — without a browser.
Gnu Privacy Guard (GPG) is free and open source software capable of encrypting, decrypting and digitally signing messages and files. It also generates and manages the public and private keys needed to do so.
Enigmail is a Thunderbird add-on that allows you to access the encryption and authentication features provided by GnuPG, which must be installed for Enigmail to work.
1.0 Things you should know about Thunderbird before you start
You will need at least one email account to use Thunderbird. If you want to create a new account to use with Thunderbird, refer to the RiseUp guide.
Like all email clients, Thunderbird makes a copy of your messages available on your computer. This includes the emails you send as well as those you receive. As a result, it is particularly important that you implement device encryption (such as FileVault) when you decide to use Thunderbird.
Thunderbird cannot protect your device if you open malicious attachments or click on malicious links. Do not open unsolicited attachments and exercise caution when clicking on links that were sent to you by email. Learn how to Protect your device from Malware and Hackers guide.
1.1 Other tools like the Thunderbird
Thunderbird is available for Mac OS X, GNU/Linux and Microsoft Windows. Securely managing multiple email accounts is a complex task, and we strongly recommend Thunderbird for this purpose. However, if you prefer to use an alternative we recommend the following free and open source tools:
- Claws Mail is available for GNU Linux and Microsoft Windows
- Sylpheed is available for Mac OS X, GNU Linux and Microsoft Windows
- K9 Mail and OpenKeychain are available for Android
- Mailpile has a beta available for GNU/Linux and Microsoft Windows (and should be available for Mac OS X in the future)
The security advantages of Thunderbird are significant, particularly when compared to commercial alternatives like Microsoft Outlook.
2.1 Install Thunderbird
To install Thunderbird, follow the steps below:
Step 1. Browse to the Thunderbird download page at https://www.mozilla.org/en-US/thunderbird
Figure 1: The Thunderbird download page
Step 2. Click[Free Download] to choose a location for the Thunderbird disk image
Figure 2: Choosing a location for the disk image
Step 3. Make sure DiskImageMounter is selected next to Open with and click[OK] to download the disk image
Figure 3: Downloading the Thunderbird disk image
After your browser has downloaded the disk image, Finder will mount it so you can install Thunderbird into your Applications folder
Figure 4: Inside the Thunderbird installer disk image
Step 4. Within the folder shown in Figure 4, drag the Thunderbird application into the Applications folder as shown below
Figure 5: Dragging Thunderbird into the Applications folder
Step 5. Dismount the Thunderbird installer disk image by pressing Command-E while the disk image window is active
2.2 Add an email account to Thunderbird
To add an email account to Thunderbird, follow the steps below.
Step 1. LaunchThunderbird
Figure 1: First launch of Thunderbird
Step 2. (Optional) Uncheck the Always perform this check when starting Thunderbird box
Step 3. Choose whether or not you want to make Thunderbird your default Email client
- To set Thunderbird as your default email client, make sure the box next to E-mail is checked and click[Set as Default]
- To keep your current default email client, click[Skip Integration]
Note: If you use Apple Mail (the email client that comes with Mac OS X), you might want to Skip Integration for now
If you have not yet added an email account, Thunderbird will display the Would you like a new email address? screen
Figure 2: Thunderbird offering to help you create a new email address
Step 4. Click[Skip this and use my existing email] to open the Mail Account Setup screen
Figure 3: The Mail Account Setup screen
Step 5. Type the name, email address and password that correspond to the account you wish to access using Thunderbird
Step 6. Uncheck the box next to Remember my password
Figure 4: Adding account information to the Mail Account Setup screen
Step 7. Click[Continue]. Thunderbird will check the configuration of the email service you have entered.
Figure 5: Thunderbird after verifying the configuration of an email service
You probably want to leave 'IMAP (remote folders)' selected. IMAP stores the master copy of your email folders (including the Inbox, Drafts, Templates, Sent and Trash folders) on the server and makes a local copy on your device. This allows you to access the same messages from multiple devices while keeping your folders in sync. (POP, on the other hand, retrieves your messages from the server and stores them on the first device to which they are downloaded. This does not mean they are actually deleted from the server, but it does make it much more difficult to access your email from multiple devices.)
Important: Make sure that both the Incoming and Outgoing information shown on the screen above display SSL (Secure Sockets Layer) or STARTTLS (Start Transport Layer Security). Either one indicates that your email provider supports basic encryption.
Step 8. Click[Done] to create your account and enter the main Thunderbird interface.
Figure 6: The main Thunderbird interface
Note: To add another email account, clickFile in the menu bar and selectNew > Existing Mail Account. This will activate Figure 3, above. Then, simply repeat Steps 5 through 8.
Each time you launch Thunderbird, you will be asked to enter the passphrase for each account you have added.
Figure 7: The Mail Server Password Required screen
Step 9. Type your passphrase
Figure 8: Entering a password into the Mail Server Password Required screen
Step 10. Click[OK] to sign in to your account(s) using Thunderbird
This section explains how to configure Thunderbird's preferences to help defend your system against attacks that originate in emails. For more information, see Protect yourself from Malware & Hackers.
3.1 Disable HTML email
Thunderbird allows you to include colours, fonts, images and other formatting in the emails you write. It does this by sending messages that include HTML — the same technology used in webpages — rather than just basic text. It also has the ability to display HTML messages sent to you by others. Unfortunately, viewing HTML email can expose you to some of the attacks used to target web browsers. And writing HTML email sometimes prevents GnuPG encryption from working properly.
To display HTML emails as plain text, follow the steps below:
Step 1. Click to display the Thunderbird Menu
Step 2. SelectView > Message Body As > Plain Text
Figure 1: Disabling the display of HTML email
To write email in plain text, follow the steps below:
Step 1. Click to display the Thunderbird Menu
Step 2. Select Options > Account Settings
Step 3. Select Composition & Addressing under your email address
Figure 2: The Composition & Addressing screen with Compose messages in HTML format unchecked*
Step 4. Uncheck the Compose messages in HTML box.
Step 5. Click[OK]
3.2 Configuring Thunderbird's Security preferences
To modify Thunderbird's security preferences, follow the steps below:
Step 1. Click to activate the Thunderbird menu bar
Step 2. SelectPreferences > Preferences
Step 3. Click the Security tab
Figure 1: Thunderbird's security preferences screen
Step 4. Click the Passwords sub-tab
Figure 2: The Passwords tab
To view or remove email account passphrases stored on your computer, click[Saved Passwords]

Figure 3: The Saved Passwords window
To remove all of the passphrases saved by Thunderbird, click[Remove All]. You can also remove individual passphrases
Important: We recommend that you protect your passphrases using a tool designed specifically for that purpose. See KeePassX for more information. However, if you do intend to allow Thunderbird to remember them for you, it is extremely important that you set a master password so that Thunderbird can encrypt your other passwords. In fact, even if you do not want Thunderbird to store your email account passphrases, you might still want to set a master password. Doing so will ensure that Thunderbird encrypts any passphrase you might accidentally ask it to save. If you do this, be sure to remember your master password or record it somewhere safe (like in a KeePassX database). And be aware that Thunderbird will ask you for that master password every time you restart the application.
Step 5. Check the Use a master password box to activate the following screen
Figure 4: Change Master Password window
Step 6. Type a strong passphrase into both fields and click[OK].
3.3 Configuring Thunderbird's privacy preferences
Cookies contain information that is sent to your browser by the websites you visit. When you return to those sites, you send the corresponding cookies back to them, along with your request for content. Cookies are used for a number of reasons. For example, websites that require you to sign in often use them to remember whether or not you have done so. But cookies can also be used to track your online activities.
Thunderbird accepts cookies primarily to support RSS feeds and newsgroups, not for email. We recommend that you disable support for cookies in Thunderbird. If this prevents you from using a feature of Thunderbird that you need, you can always go back and enable it.
You can tell Thunderbird not to accept cookies by following the steps below:
Step 1. Click to activate the Thunderbird menu bar
Step 2. SelectPreferences > Preferences
Step 3. Click the Privacy tab
Figure 1: The Privacy tab
Step 4.Uncheck the following boxes:
- Allow remote content in messages. (You can still enable remote content on a per-message basis.)
- Remember web sites and links I've visited.
- Accept cookies from sites
GNU Privacy Guard (GnuPG or GPG) is free and open source encryption software developed by the GNU Project. It is compliant with the OpenPGP standard and was designed to inter-operate with Pretty Good Privacy (PGP), a commercial equivalent developed by Phil Zimmermann and maintained by Symantec.
On a Mac, the GPG Suite bundle provides an easy way to install GnuPG. Enigmail is a Thunderbird add-on that allows you to access GnuPG's encryption features from within Thunderbird.
GnuPG relies on a form of public-key cryptography that requires each user to generate his or her own pair of keys. This key pair can be used to encrypt, decrypt and sign digital content such as email messages. It includes a private key and a public key:
Your private key is extremely sensitive. Anyone who managed to obtain a copy of this key would be able to read encrypted content that was meant only for you. They could also sign messages so they appeared to have come from you. Your private key is, itself, encrypted to a passphrase that you will choose when generating your key pair. You should choose a strong passphrase and take care not to let anyone gain access to your private key. You will use your private key to decrypt messages sent to you by those who have a copy of your public key.
Your public key is meant to be shared with others and can not be used to read an encrypted message or fake a signed one. Once you have a correspondent’s public key, you can begin sending her encrypted messages. Only she will be able to decrypt and read these messages because only she has access to the private key that matches the public key you are using to encrypt them. Similarly, in order for someone to send you encrypted email, they must obtain a copy of your public key. It is important to verify that the public key you are using to encrypt email actually does belong to the person with whom you are trying to communicate. If you or your correspondent are tricked into encrypting email with the wrong public key, your conversation will not be secure.
GnuPG and Enigmail also let you attach digital signatures to your messages. If you sign a message using your private key, any recipient with a copy of your public key can verify that it was sent by you and that its content was not tampered with. Similarly, if you have a correspondent's public key, you can verify his digital signatures.
4.1 Install GPG Suite and Enigmail
This section walks you through the installation of GPGSuite and Enigmail.
4.1.1 Install GPG Suite
To install GPG Suite, follow the steps below:
Step 1. Browse to the GPG Suite download page at https://gpgtools.org/gpgsuite.html
Figure 1: The GPG Suite download page
Step 2. Click[Download GPG Suite] to download the installer disk image
Figure 2: Choosing what to do with the GPG Suite installer disk image when it is downloaded
Step 3. Make sure DiskImageMounter (default) is selected next to Open with and click[OK]
Figure 3: Downloading the GPG Suite installer disk image
After your browser has downloaded the disk image, Finder will mount it so you can install GPG Suite
Figure 4: Inside the GPG Suite installer disk image
Step 4. Double-click the Install icon on the left to begin the process of installing GPG Suite.
Figure 5: The GPG Suite installer
Step 5. Click[Continue] to choose a location for the installation
Figure 5: Accepting the default install location for GPG Suite
Step 6. Click[Install] to install to enter your login passphrase
Figure 6: The GPG Suite installer asking for your login passphrase
Step 7. Type the passphrase you use to log in to your computer
Step 8. Click[Install Software] to install GPG Suite
Figure 7: The installation of GPG Suite
When the installer is done, it will launch the GPG Keychain application so that you can generate your GnuPGpublic and privatekey pair.
Figure 8: The GPG Suite key generation screen
We will return to key generation in Section 4.2. For now, you can quit GPG Keychain by following the steps below.
Step 9. Click[Cancel] to close the key generation screen
Step 10. To quit GPG Keychain, pressCommand-Q.
Next, you should quit the installer and dismount the installation disk image by following the steps below:
Step 11. Switch back to the Install GPG Suite installer application
Figure 9: The GPG Suite installer when it is done
Step 12. Click[Close] to quit the installer
Step 13. Switch back to Finder
Figure 10: Inside the GPG Suite installation volume
Step 14. Dismount the GPG Suite installer disk image by pressing Command-E while the disk image window is active
4.1.2 Install Enigmail
To install Enigmail, follow the steps below.
Step 1. LaunchThunderbird and sign in to your account
Figure 1: Thunderbird
Step 2. Click
Figure 2: Opening the Add-ons Manager
Step 3. SelectAdd-ons to open the Add-ons Manager
Figure 3: The Thunderbird Add-ons Manager
Step 4. Type 'Enigmail' into the search field in the upper, right-hand corner of the Add-ons Manager and pressEnter
Figure 4: Finding the Enigmail add-on
Step 5. Click[Install] next to the entry for Enigmail to begin installing the add-on.
Figure 5: Installing the Enigmail add-on
When Thunderbird is done installing the add-on, it will let you know
Figure 6: The Enigmail add-on installed
Step 6. ClickRestart now to restart Thunderbird and complete the installation of Enigmail
When Thunderbird restarts, it will automatically launch the EnigmailSetup wizard
Figure 7: The Enigmail Setup wizard
4.2 Generate encryption keys and configure Enigmail
This section covers the generation of a GnuPGkey pair and the configuration of Enigmail.
4.2.1 Generate encryption keys
To generate a GnuPGkey pair, follow the steps below.
Step 1. Click and selectEnigmail > Setup Wizard
Figure 1: Launching the Enigmail Setup Wizard
Step 2. This will open the GnuPGSetup Wizard
Figure 2: The Enigmail Setup Wizard
Step 3. Make sure the I prefer a standard configuration (recommended for beginners) option is selected and click[Continue]
You may see a warning about your GnuPG version, as shown below
Figure 3: GnuPG version warning
If you do, click[OK]. Otherwise, simply continue on to the Create Key screen shown in Figure 4, below.
Figure 4: Choosing a passphrase for your new GnuPG key pair
Step 4. Choose a strong passphrase and type it into the two fields shown on this screen.
Figure 5: Choosing a passphrase for your GnuPG key pair
Note: This passphrase will be used to encrypt your private key, which is what allows you to sign emails you send and decrypt emails you receive. It should not be shared with anyone. As such, it is important that you choose a strong passphrase and that you do not forget it. You can learn more from the Create and maintain strong passphrases guide.
Step 5. Click[Continue] to generate your GnuPG key pair
Figure 6: Enigmail generating a new GnuPG key pair
When Enigmail has finished generating your GnuPG key pair, it will let you know, and a Generate Revocation Certificate button will appear.
Figure 7: Enigmail ready to generate a revocation certificate
You should generate a revocation certificate so you can let others know when a particular key is no longer valid. This may happen if you:
- Stop using a keypair
- Lose a private key
- Forget the passphrase for a private key
- Believe a private key has been compromised or shared with others
It is particularly important that you generate a revocation certificate if you plan to upload your public key to a keyserver. There is no other way to 'delete' a key once you have uploaded it, and you do not want old or compromised keys sitting around on a keyserver confusing people.
Step 6. Click[Create Revocation Certificate] to enter your login passphrase
Figure 8: Enigmail asking for your login passphrase
Step 7. Type the passphrase you chose when creating your GnuPGkey pair
Step 8. Click[OK] to choose a name and location for your revocation certificate
Figure 9: Choosing a name and location for your revocation certificate
In this example, we will put the revocation certificate in the Documents folder, but you can store it anywhere safe.
Step 9. Click[Save] to display Enigmail's warning about the importance of keeping your revocation certificate safe.
Figure 10: Revocation certificate warning
Step 10. Click[OK] to return to the Setup Wizard
Figure 11: The Enigmail Setup Wizard
Step 11. Click[Continue] to complete the key generation process
Figure 12: The Enigmnail Thank you screen
Step 12. Click[Done] to exit the Setup Wizard and return to Thunderbird
4.2.2 Configure Enigmail to work with your email account
You must enable Enigmail for each email account, in Thunderbird, through which you want to send and receive GnuPG encrypted email. To do so, follow the steps below.
Step 1. Click and selectPreferences > Account Settings
Figure 1: Opening Thunderbird's Account Preferences
This will open the Account Preferences screen
Figure 2: Thunderbird's Account Preferences screen
Step 2. ClickOpenPGP Security under the account with which you want to send and receive encrypted email
Figure 3: Enigmail's OpenPGP settings for an email account in Thunderbird
This screen allows you to set various Enigmail preferences related to email encryption. If you generated your GnuPGkey pair by following the instructions in the previous section – after adding a single account to Thunderbird – that account should already be configured to work with Enigmail. It should also be linked to the key pair you generated. If it is not, continue with Step 3, below. If it is, you can skip to Figure 6.
Step 3. Check the box next to Enable OpenPGP support (Enigmail) for this identity
Step 4. Click[Select Key..] to open the Select OpenPGP Key for Encryption window
Figure 4: Enigmail's Select OpenPGP Key for Encryption screen
Here are the things that I love about the Win32 Disk Imager:. /win32diskimager-for-mac.html. There is no need for you to install the program.
Step 5. Select the key pair you want to use for this email account
Figure 5: Selecting a key pair for a particular email account in Thunderbird
Step 6. Click[Select Key..] to link this key pair with this email account and return to the OpenPGP Security settings screen
Below, we recommend two optional, non-default settings.
Figure 6: Configuring Enigmail for this email account
Step 7. Check the Use PGP/MIME by default box
With this box checked, Enigmail is better able to encrypt email attachments, including their filenames.
Step 8. Check the sign encrypted messages box
With this box checked, Enigmail will digitally sign all encrypted email sent through this account unless you specifically tell it not to. Unencrypted messages will remain unsigned by default.
Step 9. Click[OK] to return to Thunderbird
4.2.3 Viewing and managing your key properties
Once you have generated your GnuPGkey pair and configured your email account to work with Enigmail, you can view and manage the properties of your key pair by following the steps below.
Step 1. Click and selectEnigmail > Key Management
Figure 1: Opening Enigmail's Key Management screen
This will activate your Enigmail Key Management screen
Figure 2: Enigmail's Key Management screen
Step 2. Double-click the name of your key pair to view or edit its properties
Figure 3: key pair properties
The Key Properties window displays important information about your GnuPGkey pair:
- Key ID: The key ID shown above for ekaterina@riseup.net is 0xFA4CD1D2. (This corresponds to the last eight digits of the full key fingerprint below.)
- Key fingerprint: The key fingerprint for the same key pair is 93A4 EDCD 2C9A B746 F209 AD2A 0EF3 0EA3 FA4C D1D2. Your key fingerprint is not something you need to keep secret. In fact, it is meant to be shared.
- Expiration date: This key pair will no longer work after 18 December, 2020.
Before others can send you encrypted email, they must have a copy of your public key. You can learn more about sharing keys in Section 4.3. Your key fingerprint is an important part of how others can make sure that the key they have for you is actually yours. We discuss key verification in Section 4.4.
(Optional) Changing the expiration date of a key pair
If you need to change the expiration date of your GnuPGkey pair, follow the steps below. This is most useful as a way to extend the expiration date, as it approaches, if you need more time to generate a new key pair and inform those with whom you communicate using encrypted email.
Step 1:Click[Select action..] and selectChange Expiration Date
Figure 4: Changing the expiration date of a GnuPG key pair
This will activate the change expiration date screen shown below
Figure 5: Changing the expiration date of a GnuPG key pair
Note: The number of years shown at the bottom of the screen does not necessarily match the current expiration date. If you click [OK] without changing anything, you may temporarily reduce the life-span of your key pair.
(Optional) Changing the passphrase for a private key
If you would like to change the passphrase that protects your private key, follow the steps below.
Step 1. Click[Select action..] and selectChange Passphrase
Figure 6: Entering a private key passphrase
Step 2. Type the passphrase for your private key
Step 3. Click[OK]
Step 4. Choose a new passphrase, type it into both fields and click[OK]
4.3 Exchanging public keys
Before you can start sending encrypted email messages to one another, you and your correspondents need to exchange public keys. You also need to confirm the validity of any key you receive by confirming that it really belongs to the person you believe sent it.
4.3.1 Sending your public key as an email attachment
To send a public key using Enigmail both you and your correspondent will need to perform the following steps:
Step 1: Open Thunderbird and click[Write] to write an email.
Step 2: Select Enigmail > Attach Public Key..
Step 3: Select the key you would like to send (typically the one associated with the email account you are currently using).
Figure 1: Selecting which public key to attach
Step 4:Click[Send]. Your key will not appear as an attachment until just before the email is sent.
Figure 2: An attached public key about to be sent
Step 5:Type your GnuPG passphrase and press Enter if prompted
4.3.2 Importing a public key attached to an email
Both you and your correspondent must follow the steps below to import one another's public keys.
An attached public key should be visible in the lower, left-hand corner of the email in which it was sent:
Figure 1: A public key attached to an email
Gpg Encryption For Mac
Step 1. Hold down Control and click the attachment
Figure 2: The context menu for a public key attached to an email
Step 2. SelectImport OpenPGP Key to import your correspondent's public key
Figure 3: Public key successfully imported
Step 3. Click[OK] to close the window telling you that the key(s) were successfully imported.
Enigmail's Key Management screen should now show your correspondent's public key:
Step 4. Click to activate the Thunderbird menu
Step 5. SelectEnigmail > Key Management
Figure 4: A new public key displayed in Enigmail's Key Management screen
4.4 Validating and signing public keys
You should now verify that the key you have imported actually belongs to the person you believe sent it to you. This is a process that you (and your email correspondents) should go through for each public key you receive. Once you verify the key, you will sign it so that GnuPG knows that it is valid.
4.4.1 Validating someone else's public key
To validate your correspondent's public key, contact him using a means of communication that allows you to be absolutely certain that you are talking to the right person. In-person meetings are best, but voice and video conversations are acceptable if you are confident you can recognise his voice or appearance. This conversation does not have to be confidential, as long as you refrain from discussing sensitive topics. You will be exchanging public keyr fingerprints, which need not be kept secret.
Both you and your correspondent should verify the fingerprints of the public keys you have exchanged. A fingerprint is a unique series of numbers and letters that identifies a GnuPGkey pair. You can use the EnigmailKey Management screen to view the fingerprint of the key pairs you have generated and of the public keys you have imported.
To view the fingerprint of a particular key pair, follow the steps below.
Step 1. Click to activate the Thunderbird menu
Step 2. SelectEnigmail > Key Management
Step 3:Double-click a key pair to open the EnigmailKey Properties window.
Figure 1: Enigmail's Key Properties screen
In the Key Properties window, you will be able to see the fingerprint of the selected key pair. For example, the fingerprint of ekaterina@riseup.net is 93A4 EDCD 2C9A B746 F209 AD2A 0EF3 0EA3 FA4C D1D2
Your correspondent should carry out these steps as well. So, to verify fingerprints:
- Read the fingerprint of your keypair to your correspondent
- Have him verify that the fingerprint he has for your public key matches what you just told him
- Have your correspondent read you the fingerprint for his keypair
- Verify that the fingerprint you have for his public key matches what he just told you
If the fingerprints don't match, exchange public keys again and repeat the process.
Note: Because key fingerprints are not themselves sensitive, you can easily write down the fingerprint that your correspondent reads off to you. Then, when you have more time, You can verify that it matches the fingerprint you have for his public key using Enigmail's Key Management screen. (This is also why some people print their GnuPG fingerprints on their business cards.)
4.4.2 Signing someone else's valid public key
Once you have verified a correspondent's key, you should sign it. This will tell Enigmail to remember that you consider this key valid.
Important: If you sign some else's public key, then make your signed copy of their key available publicly, it can easily expose the fact that you exchange sensitive information with that person. To prevent this from happening by accident, always check the Local signature box when signing a correspondent's public key.
You can sign a validated public key by following the steps below.
Step 1. Click to activate the Thunderbird menu
Step 2. SelectEnigmail > Key Management
Step 3. Hold down Control and click the public key you want to sign.
Figure 1: Signing someone else's public key
Step 4. SelectSign Key
Figure 2: Sign keys locally to avoid exposing your connection to their owners
Step 5. Make sure your key pair is selected next to Key for signing
Step 6. ClickI have done very careful checking
Note: Other options (such as I have not checked at all) may not allow you to send encrypted message to the owner of this key. And, due to a bug in Enigmail, it may be difficult to change this setting later. Accordingly, we recommend that you always select I have done very careful checking when signing a correspondent's public key.
Step 7. Check the Local signature (cannot be exported) box
Important: Unless you are very confident with GnuPG – and know for a fact that the owner of this public key wants your signature of his key to be public – you should check this box.
Step 8. Click[OK]
Figure 3: Entering the passphrase for your private key to sign someone else's public key
Step 9. Type the passphrase for your private key when asked
Step 10. Click[OK] to sign this public key. This will tell Enigmail that you have verified the identity of its owner, which will allow you to send him encrypted email.
4.5 Encrypting and decrypting email messages
GnuPG only protects the content of email and attachments you encrypt. The following information is never encrypted:
- The Subject line
- The sender's email address
- Recipients' email addresses
- Any real names that might associated with senders and recipients. (Elena S. Katerina <ekaterina@riseup.net>, for example.)
Furthermore, if you configure Enigmail to use Inline PGP instead of PGP/MIME, the filenames of attachments you send will remain unencrypted.
So choose your subject lines carefully, consider creating a GnuPG key for at least one email account that does not include your real name and always use PGP/MIME.
Finally, when you send encrypted email, rest assured that a copy — encrypted to your public key — will be placed in your Sent mail folder.
4.5.1 Sending encrypted email
Once you and your correspondent have successfully imported, validated and signed one another's public keys, you can begin exchanging encrypted messages.
You can encrypt the content of your email messages by following the steps below:
Step 1. In Thunderbird, click[Write] and compose an email to a recipient for whom you have a signed public key
Figure 1: Thunderbird's Compose Window
Step 2. ClickEnigmail:, in the upper, left-hand corner of the compose window, just beneath the [Send] button.
Figure 2: Enabling encryption and signing
Step 3. Check the Encrypt Message box
Step 4. Check the Sign Message box
Step 5. Click[OK] to return the compose window
Once you have entered a To: address for which you have a verified public key, the following message should appear in the upper, right-hand corner of the window:
How To Use Gpg For Mac
Figure 3: Enigmail letting you know that it is ready to encrypt and sign a message
Step 6. Click[Send]
Step 7. Type the passphrase for your private key
Step 8. Click[OK] to send your (encrypted and signed) message.
4.5.2 Decrypting an email from someone else
When you click on an encrypted message, Enigmail will prompt you for the passphrase to your private key so it can decrypt the message. Type your passphrase and click[Unlock].
Figure 1: A decrypted message with a verified signature
Enigmail will display some information at the top of the message. In the figure above, for example, 'Decrypted message; Good signature from mansour' tells you that:
- The message was encrypted using your public key (which can be done by anyone)
- You successfully decrypted it
- It was signed by someone with the private key that corresponds to the mansour@riseup.net public key that you have imported
- You have signed that mansour@riseup.net public key, hopefully after verifying that it belongs to the real Mansour.
Q: What happens if I just install Enigmail and not GnuPG?
A: That's simple, really. Enigmail just won't work. After all, it's the GnuPG software that provides the encryption engine that Enigmail uses.
Q: How many email accounts can I set up in Thunderbird?
A: As many as you like! Thunderbird is an email manager and can easily handle 20 or more email accounts!
Q: My friend has a Gmail account. Should I convince him to install Thunderbird, Enigmail and GnuPG?
Kleopatra Pgp Mac
A: That would be ideal. Just make sure he configures all of his security settings in exactly the same way as you did. Then the two of you will have an extremely effective way of communicating in privacy and safety!
Mac Install Gpg
Q: Remind me one more time, which parts of an email message does Enigmail encrypt?
Gpg Keychain For Mac
A: Enigmail only encrypts the content of messages. Subject lines will not be encrypted, nor will sender and recipient email addresses (or the names associated with those addresses). So, choose your subject lines carefully and consider creating a GnuPG key for at least one email account that does not include your real name.
Q: I still don't understand the purpose of digitally signing my messages.
A: A digital signature proves that you're the real sender of a particular message and that the message hasn't been tampered with on its way to your intended recipient. Think of it as the electronic equivalent of the wax seal on an envelope, which contains a very important letter.